CYBER SECURITY
SERVICES
The evolution of cyber
threats has seen a shift from
isolated incidents of
malware to sophisticated,
widespread attacks with
significant impacts on

CYBER SECURITY
SERVICES
The evolution of cyber threats has seen a shift from isolated incidents of
malware to sophisticated, widespread attacks with significant impacts on

Cybersecurity has
become an
essential priority
The evolution of cyber threats has seen a
shift from isolated incidents of malware to
sophisticated, widespread attacks with
significant impacts on individuals,
businesses, and society as a whole.
Cybersecurity has
become an
essential priority
The evolution of cyber threats has seen a shift from isolated incidents of malware to sophisticated, widespread attacks with significant impacts on individuals, businesses, and society as a whole.

Automated Pentest
Find vulnerabilities,
infrastructure and/or
development issues.
Vulnerabilities Tools
Implementation
Essential to guarantee the cybersecurity of any company. They enable the proactive identification and correction of system flaws before they can be exploited by external threats.
Periodic Reports
Valuable insights into vulnerabilities and incidents, enabling rapid corrective action. Maintaining a reporting routine strengthens your security posture and ensures ongoing protection of data and systems.
Automated Pentest
Find vulnerabilities,
infrastructure and/or
development issues.
Vulnerabilities Tools
Implementation
Essential to guarantee the cybersecurity of any company. They enable
the proactive identification and correction of system flaws before
they can be exploited by external threats.
Periodic Reports
Valuable insights into vulnerabilities and incidents, enabling rapid
corrective action. Maintaining a reporting routine strengthens your
security posture and ensures ongoing protection of data and systems.
Environment’s Vulnerability List
It enables proactive mitigation actions, strengthening overall security. Keeping this list updated ensures a safer and more resilient technological environment.
Hack the system 2 or 3 times per year
Scanning your own systems is essential to identify vulnerabilities and fix flaws before they are exploited by external threats. Ensure a more robust and resilient digital environment against cyberattacks.
Manual Pentest
Hacker inserted into the
DevOps client flow to
avoid vulnerabilities in
production;
Environment’s Vulnerability List
It enables proactive mitigation actions, strengthening overall security. Keeping this list updated ensures a safer and more resilient technological environment.
Hack the system 2 or 3 times per year
Scanning your own systems is essential to identify vulnerabilities and
fix flaws before they are exploited by external threats. Ensure a more
robust and resilient digital environment against cyberattacks.
Manual Pentest
Hacker inserted into the
DevOps client flow to
avoid vulnerabilities in
production;
Blue and Red Teams
Benefits of crisis
management
with expert
teams
The Blue Team represents the defensive
side of cybersecurity. The Red Team, on
the other hand, represents the offensive
side of cybersecurity
Red
Team
- Social Engineering
- Penetration Testing
- Exploitation of Security Weaknesses
- Provides Insights into Potential Security Gaps
Blue
Team
- Security Controls
- Monitoring Systems
- Conducting Security Assessments
- Responding to Incidents
Blue and Red Teams
Benefits of crisis
management with
expert teams
The Blue Team represents the defensive side of cybersecurity. The Red Team, on the other hand, represents the offensive side of cybersecurity
Red
Team
- Social Engineering
- Penetration Testing
- Exploitation of Security Weaknesses
- Provides Insights into Potential Security Gaps
Blue
Team
- Security Controls
- Monitoring Systems
- Conducting Security Assessments
- Responding to Incidents
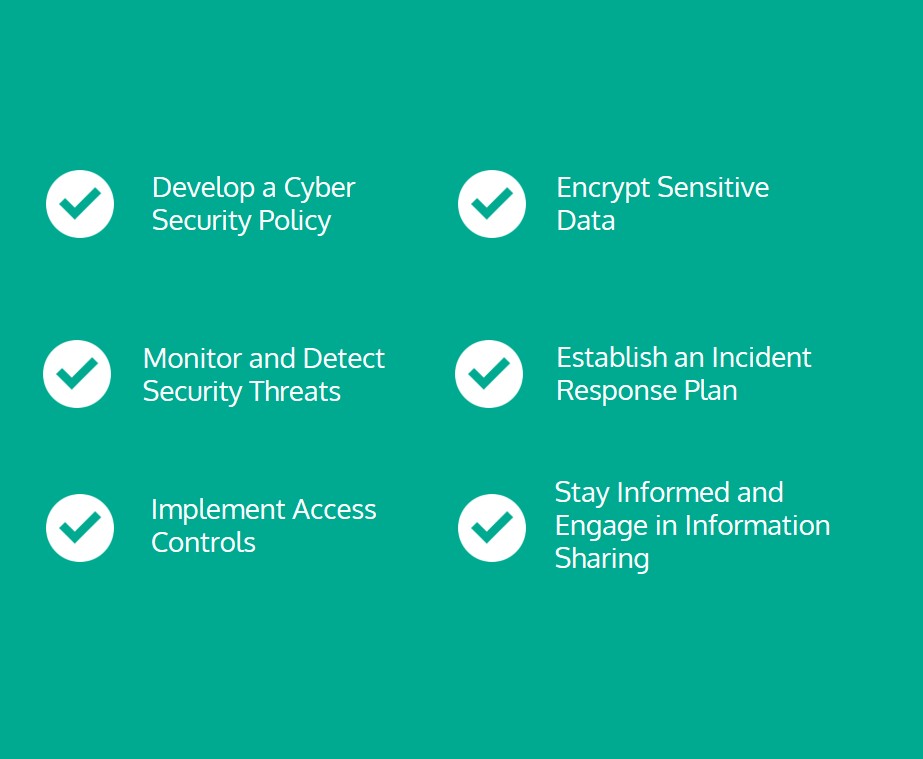
Do not suffer inherent risks
- Defense Against Cybercrime
- Prevention of Financial Loss
- Preservation of Reputation
- Protection of Critical Infrastructure
- Protection of Sensitive Information
“Meet the real
needs of
companies with
creativity,
technology and
tools to provide
excellence in
security”
Ensure now that your company can continue
its operations with maximum peace of mind
and security
Do not suffer inherent risks
- Defense Against Cybercrime
- Prevention of Financial Loss
- Preservation of Reputation
- Protection of Critical Infrastructure
- Protection of Sensitive Information
“Meet the real needs of
companies with creativity,
technology and tools to
provide excellence in
security”
Ensure now that your company can continue its operations with maximum peace of mind and security